The Evolving World of Cybersecurity: A Simple Guide to Data Protection
In today's digital age, where data is the new gold and cyber threats are constantly evolving, executive-level leaders are on the front lines, entrusted with the critical task of ensuring that their organizations' valuable assets are safeguarded and preserving the unwavering trust of their stakeholders.
According to a recent study by MarketsandMarkets, the global cybersecurity market is expected to grow to $305.4 billion by 2025, up from $176.4 billion in 2022.
As demonstrated by recent data breaches, the digital landscape is fraught with ever-evolving cyber threats that can have devastating consequences. But what exactly are the specifics of these threats? What are the costs of a successful attack?
In this blog, we'll break down the finer details of navigating the complex world of cybersecurity and data privacy, offering insights on protecting sensitive data and fortifying your defenses against these evolving threats.
The Growing Significance of Cybersecurity and Data Privacy
In an era defined by digital transformation, data has become the lifeblood of modern enterprises. As businesses leverage technology for efficiency and competitiveness, the volume of sensitive data continues to soar.
Sensitive data, including customer information, intellectual property, and financial records, is the cornerstone of business operations. It's easy to see why safeguarding this data is pivotal in maintaining trust and competitiveness.
Cyber threats have morphed into sophisticated and multifaceted adversaries. The necessity for resilience has never been more urgent as the digital battleground evolves continually.
Cyber threats are malicious activity targeting computer systems, networks, or devices. Cyber threats can be carried out by individuals or groups, and they can be motivated by various factors, including financial gain, espionage, or vandalism.
Flip through the deck below to learn more about specific threats and how to defend your organization against them.



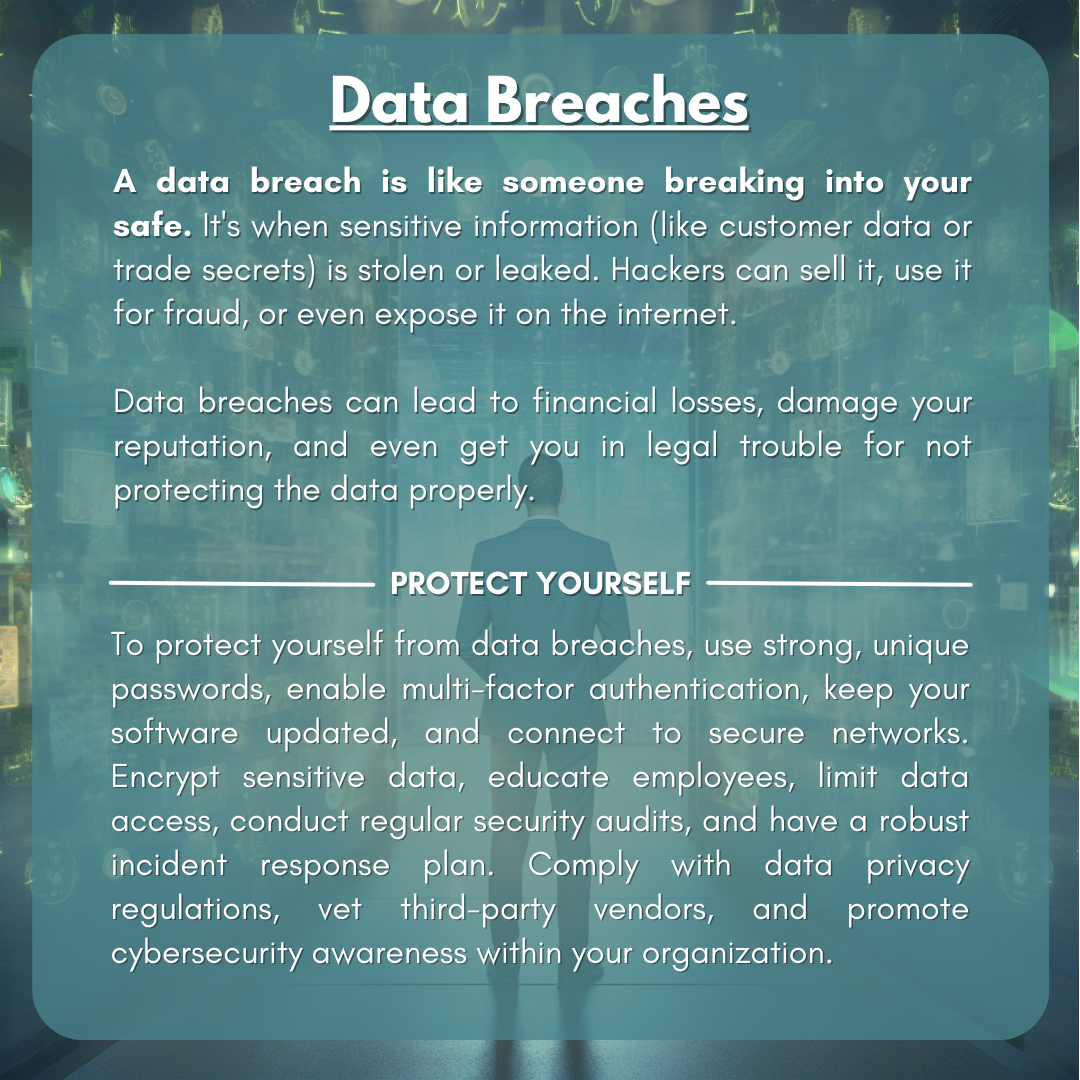


Understanding the Risks and Costs
Cyberattacks are not mere inconveniences; they translate into substantial financial losses and reputational damage. Cyber incidents cost businesses billions each year, and the numbers continue to rise.
The average data breach cost in 2023 is $4.24 million, up from $4.11 million in 2022. (IBM)
43% of cyberattacks target small businesses. (Verizon)
82% of ransomware attacks in 2021 were against companies with fewer than 1,000 employees. (Sophos)
Executive-level leaders need to understand the risks and costs of ineffective cybersecurity to make informed decisions about how to protect their businesses.
risks of ineffective cyber security
Initial financial loss: These are the costs that companies incur immediately after a cyberattack, such as the cost of investigating the attack, repairing damaged systems, and notifying customers.
Compliance-related Violations and Fines: Many industries have strict regulations governing collecting, using, and storing sensitive customer data. Companies that fail to comply with these regulations can face hefty fines and other penalties.
Loss of Customer Trust: When a company experiences a cyberattack, its customers may lose faith in its ability to protect their data, potentially leading to lost revenue and customer churn.
Damage to Brand Reputation: A cyberattack can damage a company's brand reputation and make attracting new customers and partners difficult.
Disruption of Business Operations: Downtime leads to revenue loss, sensitive data theft results in legal repercussions, and damage to critical infrastructure hampers production.
These disruptions aren't just IT problems – they're major business concerns for executive leaders who must ensure the organization's stability and reputation.
Staffing for Cybersecurity: The Skills Gap
Organizations face a significant challenge in finding qualified cybersecurity professionals. The demand for these experts far outstrips the supply. Partnering with the right talent can bolster your organization's cybersecurity posture and resilience, but the current gap within this remains significant.
Due to this enduring gap in available talent, many companies are upskilling and reskilling their existing workforces and offering cybersecurity training to all employees regardless of their job roles. This training can cover basic cybersecurity concepts, such as password hygiene and phishing awareness, as well as more advanced topics, such as incident response and threat hunting. Businesses can also offer tuition reimbursement and other incentives to encourage employees to pursue cybersecurity certifications.
Businesses can also outsource some or all of their cybersecurity needs to a third-party provider. This can be a good option for companies that do not have the resources to build and maintain their own cybersecurity team.
Executive leaders play a critical role in organizational cybersecurity.
Practical Advice for Executive Leaders
Executive leaders play a critical role in organizational cybersecurity. They must prioritize cybersecurity throughout the organization, invest in cybersecurity solutions and training, develop and test an incident response plan, and monitor the cybersecurity landscape to adapt their defenses accordingly. Additionally, executive leaders must be aware of their organization's cybersecurity risks, get involved in cybersecurity decision-making at the highest level, and hold people accountable for cybersecurity.
7 Crucial Steps to Shield Your Company Against Cyber Threats
Implementing strong security controls: This includes using firewalls, intrusion detection systems, and data encryption to protect their networks and data.
Educating employees about cybersecurity: Employees are often the weakest link in a company's cybersecurity defenses. Companies can significantly reduce their risk of being attacked by educating them about the risks of cyberattacks and how to spot and avoid phishing scams and other threats.
Having a plan for responding to cyberattacks: Even the best cybersecurity defenses can be breached, so it is essential to have a plan for responding to an attack. This includes having a team of experts to investigate the attack, contain the damage, and restore systems to normal operation.
Keeping software up to date: Cybercriminals often exploit software vulnerabilities to gain access to systems. By keeping software up to date, companies can patch these vulnerabilities, making it more difficult for attackers to gain access.
Using multi-factor authentication: Multi-factor authentication (MFA) is a security measure that requires users to provide two or more pieces of evidence to verify their identity. This can help to prevent unauthorized access to systems, even if an attacker has obtained a user's password.
Backing up data regularly: In the event of a cyberattack, companies that have backed up their data can quickly restore their systems and minimize downtime.
Invest in cybersecurity insurance: Cybersecurity insurance can help companies to recover from the financial losses that can result from a cyberattack.
By taking these steps, we can significantly reduce our risk of being attacked and minimize the damage if an attack does occur.
Conclusion
In this new age where data is the cornerstone of business, safeguarding sensitive information and maintaining cybersecurity resilience is paramount. Cyber threats will continue to evolve, with higher risks than ever. It's time for proactive measures. We urge you to take action, secure your digital future, and contact us for support.
Cybersecurity isn't just a buzzword; it's a fundamental pillar of modern business. As a parting thought, remember that in this digital age, protecting sensitive data is not just an option but an imperative. Your organization's future may depend on it!


